ØxOPOSɆC Steg Challenge 2019 | Volatility
Write-up for ØxOPOSɆC steganography challenge that involves the analysis of a volatile memory dump.

We're given an email (in EML format) with a banner and some text that is leading us to think that the email contains some sort of hidden data:
Hi,
I need someone who's able to analyse a PC, could you help me?
PS: Let's use our usual way of exchanging classified information!
--
Volatility is the constant of life!
And indeed, when we use an online steg decoder we can find a Dropbox link hidden in the image:
0c60fd56872251909cb07a749b03a34a56e1edac memdmp.zip
https://www.dropbox.com/s/ks30qs78k18lfd0/memdmp.zip?dl=0
This zip file contains only one file - memdmp - which we're going to analyse with Volatility as suggested by the email:
sudo apt-get install volatility
We start going through the various options looking for something that seems relevant, which we finally do once we see the word NOTEPAD on the clipboard.
~ volatility -f memdmp clipboard
Volatility Foundation Volatility Framework 2.6
Session WindowStation Format Handle Object Data
---------- ------------- ------------------ ---------- ---------- --------------------------------------------------
0 WinSta0 CF_UNICODETEXT 0x30115 0xe146f0b8 NOTEPAD
0 WinSta0 CF_LOCALE 0x5400fb 0xe1b75620
0 WinSta0 CF_TEXT 0x1 ----------
0 WinSta0 CF_OEMTEXT 0x1 ----------
```This leads us to search for useful data on Notepad:
~ volatility -f memdmp notepad
Volatility Foundation Volatility Framework 2.6
Process: 1864
Text:
NOTEPAD
Text:
https://bit.ly/31uALei
NOTEPAD
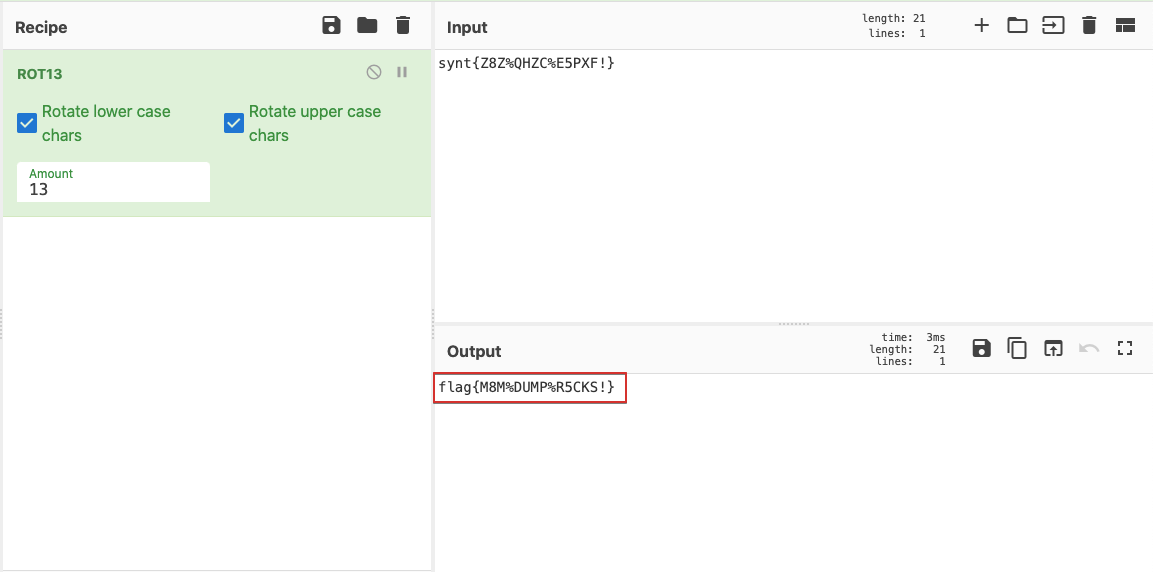
This link leads us to a file that contains a simple ROT13 cipher, which we were able to decipher this text using CyberChef: