ØxOPOSɆC | Underground Leaks - Part III
This level starts with the email message where the last level ended:
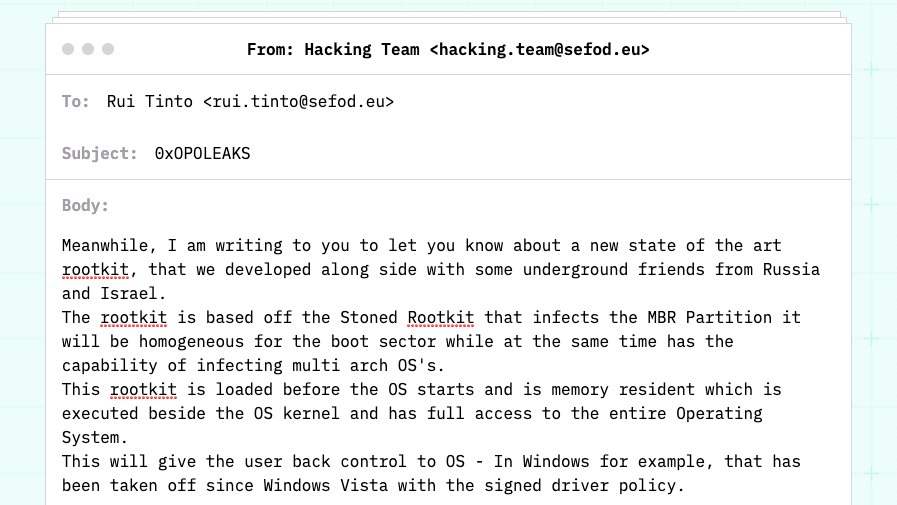
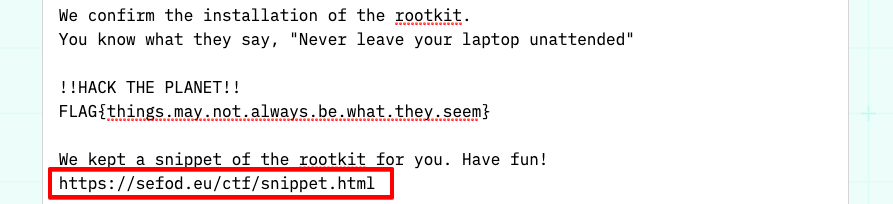
When we go to the link at the end of the message we see a simple HTML page that contains a <meta> tag that uses the http-equiv attribute:
<html>
<body>
<b>Please wait while you are being redirected...</b>
<meta http-equiv="refresh" content="5; URL=https://sefod.eu/ctf/0xOPOSEC_0x0E_DTMF_MultiTap.pdf" />
</body>
</html>As expected, 5 seconds after the page is loaded, we're redirected to https://sefod.eu/ctf/0xOPOSEC_0x0E_DTMF_MultiTap.pdf.
After a bit of trial and error, we realise that the PDF is hiding more than meets the eye (indeed "things are not always what they seem"):
$ curl -X GET https://sefod.eu/ctf/0xOPOSEC_0x0E_DTMF_MultiTap.pdf > out.file
$ file out.file
out.file: DOS/MBR boot sectorThe file contains a boot loader, which we can check by searching for the magic bytes (0x55 0xAA) in position 0x1FE.
Getting through the front door
We can run load this boot loader using qemu, an "open source machine emulator and virtualizer":
$ qemu-system-i386 -fda out.file
SeaBIOS (version 1.14.0-1)
iPXE (http://ipxe.org) 00:03.0 CA00 PCI2.10 PnP PMM+07F8F4C0+07ECF4C0 CA00
Booting from Hard Disk...
Boot failed: could not read the boot disk
Booting from Floppy...After "Booting from Floppy" we can see the intro screen:
A few seconds later this authentication form is displayed:
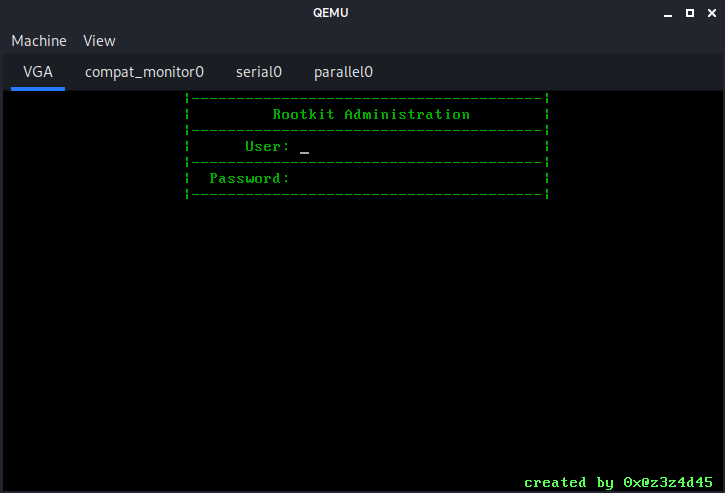
Since I didn't know the credentials, I decided to try and dump the machine's RAM using qemu-monitor's dump-guest-memory utility:
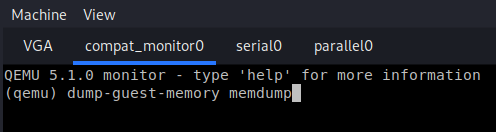
Then, by simply running strings on the memdump file I realised that the credentials were root:toor.
12 days of OPOTEAM
When we enter the credentials we see this screen:
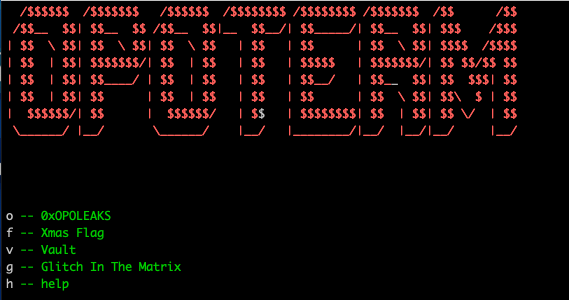
Let's check out the options!
"o" is for 0xOPOLEAKS
Simply by combining all of the letters that shouldn't be uppercase we get the flag: FLAG{SONHOSWILLKEEPYOUDREAM}
"f" is for Xmas Flag
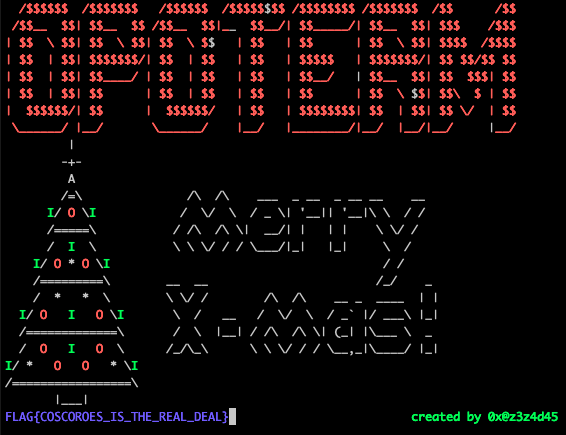
Not really a challenge, more of a Christmas message. Flag is FLAG{COSCOROES_IS_THE_REAL_DEAL}.
"v" is for Vault
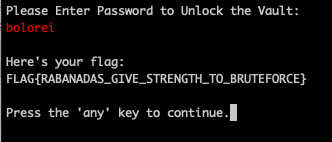
On this challenge, the prompt would only display a certain char when it matched the exact position of the flag, which meant we had to "brute-force" the solution manually, re-entering partial flags until we got the final one.
Flag is FLAG{RABANADAS_GIVE_STRENGTH_TO_BRUTEFORCE}.
"g" is for Glitch in the Matrix
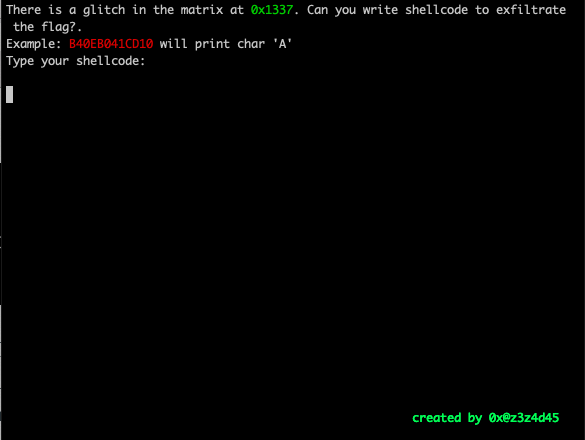
Using CyberChef we can see the instructions encoded in the example Shellcode: B40EB041CD10.

B40E MOV AH,0E
B041 MOV AL,41
CD10 INT 10
So, it seems like this code is able to print "A" since its hex value (41) is being moved to the AL register on the second operation. This means that most likely all we need to do is change the second operation with one that retrieves the value stored in 0X1337.
Since I'm not very familiar with shellcode I started by trying to retrieve the original instructions from x86 Assembly code:
$ nano glitch.asm
;glitch.asm
[SECTION .text]
global _start
_start:
mov ah, 0x0E
mov al, 0x41
int 0x10Then I converted the Assembly code to object code (.o) using NASM, and then generated the final executable using ld.
$ nasm -f elf glitch.asm
$ ld -m elf_i386 -s -o glitch glitch.o
$ ls -la
...
-rw-r--r-- 1 vagrant vagrant 192 Dec 12 07:01 glitch.asm
-rw-r--r-- 1 vagrant vagrant 432 Dec 12 07:06 glitch.o
-rwxr-xr-x 1 vagrant vagrant 4244 Dec 12 07:10 glitchFinally, I disassembled the executable using objdump, which gets us its corresponding shellcode:
$ objdump -d glitch
glitch: file format elf32-i386
Disassembly of section .text:
08049000 <.text>:
8049000: b4 0e mov $0xe,%ah
8049002: b0 41 mov $0x41,%al
8049004: cd 10 int $0x10Great, we got the original shellcode! Now we can simply change the Assembly code to retrieve the value stored at 0x1337.
$ nano glitch.asm
;glitch.asm
[SECTION .text]
global _start
_start:
mov ah,0x0E
mov al,[0x00001337]
int 0x10Let's do the same process as before to get the shellcode:
$ nasm -f elf glitch.asm
$ ld -m elf_i386 -s -o glitch glitch.o
$ objdump -d glitch
glitch: file format elf32-i386
Disassembly of section .text:
08049000 <.text>:
8049000: b4 0e mov $0xe,%ah
8049002: a0 37 13 00 00 mov 0x1337,%al
8049007: cd 10 int $0x10The shellcode is b40ea037130000cd10, let's see what happens when we enter it on the program:
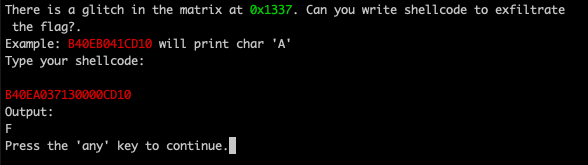
By repeating the process for the following addresses I got the complete flag: FLAG{filhoses_will not keep_you_fit}.
Taking the hint
A short while after the challenge was published, a new hint was released, a Portuguese sketch show that uses the word kunami.
With a bit of Googling I found something interesting, the Konami Code. After trying the sequence ↑↑↓↓←→←→BA on the menu I got:
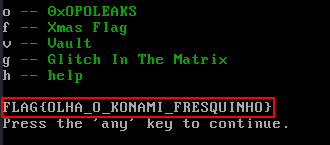
Unfortunately, I didn't get all of the flags, but you can check out the Github project and official write-up here.




