ØxOPOSɆC - HTTP2

URL: https://20.56.49.147/ | Keep calm and get the flag :)
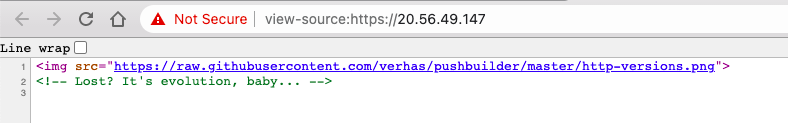
When you enter the IP directly on the browser you see only an image sourced from Github and a hidden clue: "Lost? It's evolution, baby...":
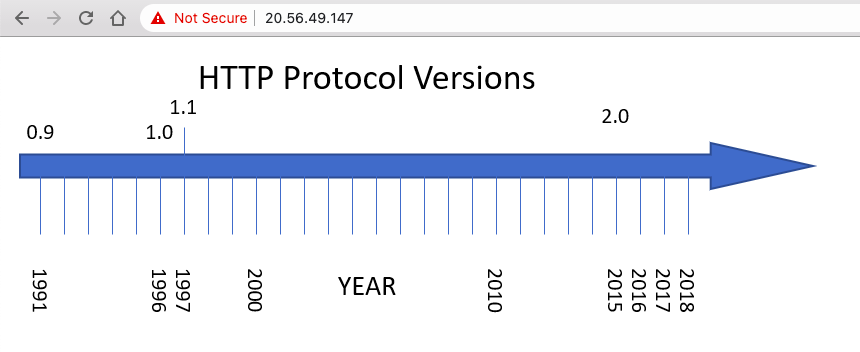
The image shows the evolution of the HTTP protocol, so it makes sense that this challenge is about some HTTP feature, either new or deprecated.
Using curl to fetch the page we see that it's served via HTTP/2, which is still kind of rare in the wild:
~ curl -ik https://20.56.49.147/
HTTP/2 200
server: nginx/1.19.10
date: Fri, 28 May 2021 11:27:17 GMT
content-type: text/html
content-length: 129
last-modified: Thu, 20 May 2021 10:10:20 GMT
etag: "60a6358c-81"
accept-ranges: bytes
<img src="https://raw.githubusercontent.com/verhas/pushbuilder/master/http-versions.png">
<!-- Lost? It's evolution, baby... -->HTTP/2 supports the Server Push feature, which basically enables servers to send assets to the client without the client having to request them, which is the perfect setup for a hidden file, like the flag.
In order to log these "hidden" request, we can use Chrome Net Export tool:
- Open up a new Chrome tab and enter
chrome://net-export/:
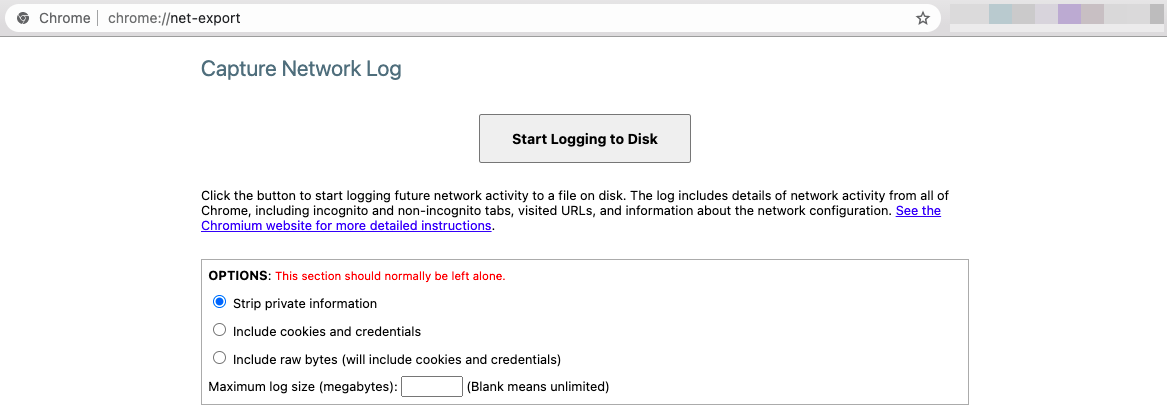
- Click "Start Logging to Disk" and choose the file where you want to write on your computer;
- Go to the challenge website and reload it;
- Go back to the Chrome Net Export tool and click "Stop Logging";
- Click "Show file" to see the log file;
- Search for the word
flagamong the results:
...
{
"params":{
"headers":[
":method: GET",
":path: /flag_652f92e28feb20d2dc22874d54cefb9b0cf96ce5c65552161fdaad4a33776394.txt",
":scheme: https",
":authority: 20.56.49.147",
"accept-encoding: gzip, deflate, br",
"accept-language: en-US,en;q=0.9,pt-PT;q=0.8,pt;q=0.7",
"user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36"
],
"id":1,"promised_stream_id":2
},
...
},
...- Access the resource and get the flag:
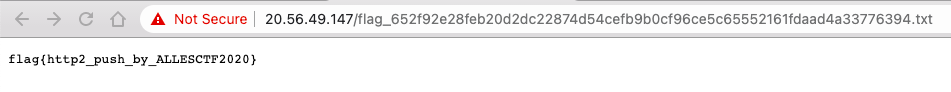
Note that alternatively, we could have simply used Nghttp2.




