ØxOPOSɆC Summer Challenge 2020 | Misc Challenges Write-up
1 . My Paste | 100
Oh no! I forgot where I left my paste. 🗑
Perhaps you can help me find it?
The source code has a little hidden clue:
<span class="challenge-desc"><br>
Oh no! I forgot where I left my paste. 🗑
<p>Perhaps you can help me find it?</p>
<p style="color: white">2WvYM5Qx</p></span>Since 2WvYM5Qx is not the correct flag, it was a matter of thinking outside the box to get to the final answer: https://pastebin.com/2WvYM5Qx.
Good job!
flag{f1n0_5Up3r_b0ck_fr3squ1nho}2. Slowly But Surely | 200
I think aliens may be trying to communicate.
What are they trying to say?
Let's take a look at some basic info about the trasmission.wav file using mediainfo:
~ mediainfo transmission.wav
General
Complete name : transmission.wav
Format : Wave
File size : 10.6 MiB
Duration : 1 min 56 s
Overall bit rate mode : Constant
Overall bit rate : 768 kb/s
Audio
Format : PCM
Format settings : Little / Signed
Codec ID : 1
Duration : 1 min 56 s
Bit rate mode : Constant
Bit rate : 768 kb/s
Channel(s) : 1 channel
Sampling rate : 48.0 kHz
Bit depth : 16 bits
Stream size : 10.6 MiB (100%)After discarding the usual audio steganography I decided to take a look at the audio's spectrogram using Sonic Visualiser.
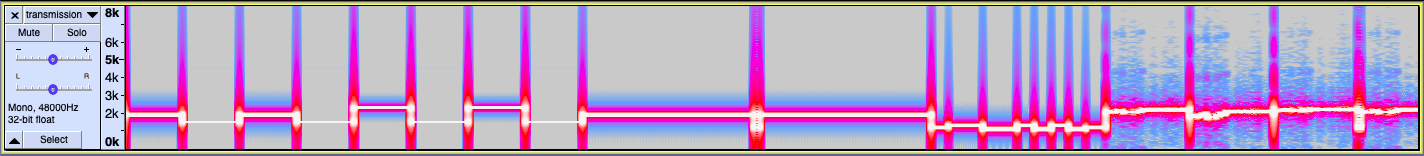
Because I'm not an expert on audio signals, I decided to Google Image search for signals that looked similar to the one shown on the spectrogram. It didn't take long until I came across this write-up with an eerily similar signal, that corresponds to a SSTV (Slow Scan TeleVision) transmission.
Slow Scan television (SSTV) is a picture transmission method used mainly by amateur radio operators, to transmit and receive static pictures via radio in monochrome or color.
This plus the hint let me know I was on the right track (however I later found out I should really be using sigid to identify the signal).
After spending a lot of time trying to make some Linux tools work for this task I had to use Windows RX-SSTV to finally decode the message:
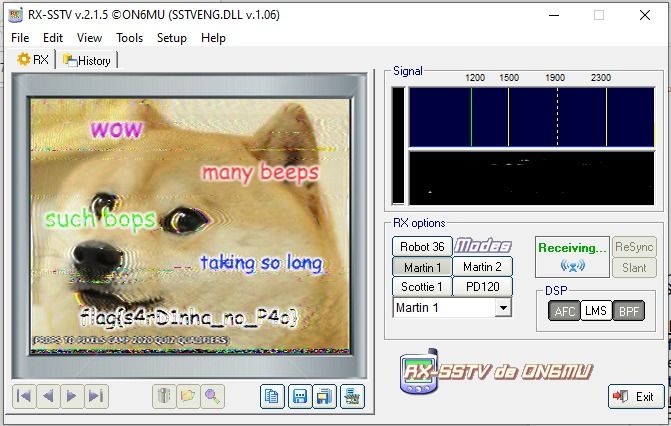
3. Run (300)

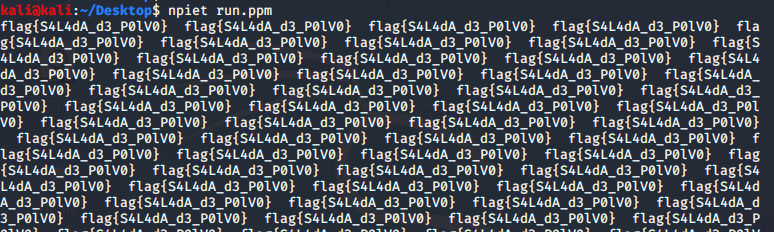
This was the only challenge I wasn't able to finish. It turns out this image is actually a program "written" in the the Piet esolang.
Piet is a stack-basedesoteric programming language in which programs look like abstract paintings. It uses 20 colors, of which 18 are related cyclically through a lightness cycle and a hue cycle. [Source]
There's a handy utility called npiet that we could use to get the flag from the file (I had to convert it to PPM first).