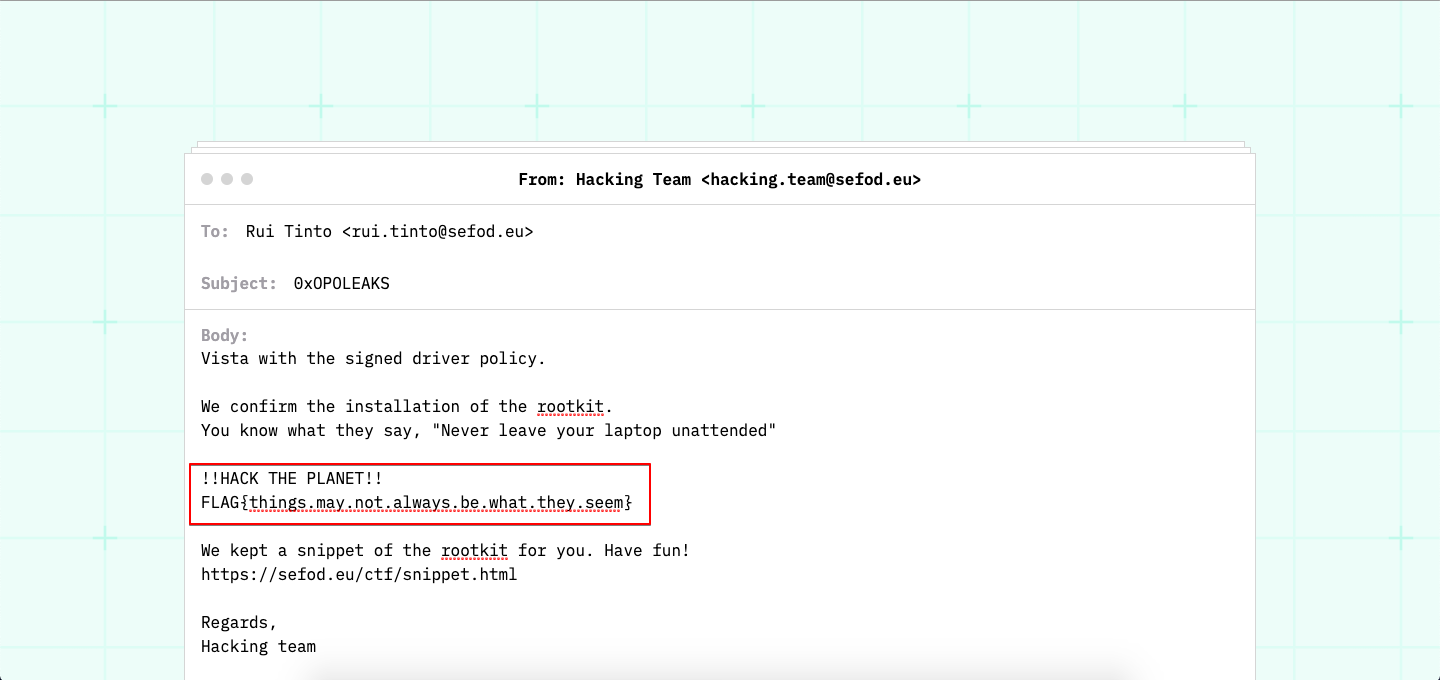
ØxOPOSɆC | Underground Leaks (Crypto) - Part II
Write-up for the second part of the Underground Leaks saga, that includes DTMF and Multi-tap Cipher.
The last mission was a success, and the government forces gave us another project, the information is short, but we know that we are on the path of the 0xOPOLEAKS. We think this is somehow related to mobile communications, can you help us?
http://sefod.eu/ctf/signal.wav
The .wav file contains a sequence of what sounds like keys being dialled on a phone, aka DTMF (Dual-tone multi-frequency signaling).
Luckily, this library does all of the hard work of decoding the tones:
~ sudo pip3 install numpy matplotlib scipy
~ git clone https://github.com/ribt/dtmf-decoder/
~ cd dtmf-decoder
~ chmod +x dtmf.py
~ ./dtmf.py [path_to_file]/signal.wav
2244485559990666766699627777So, it seems like we have another cipher to crack. Since this cipher includes numbers being repeated, but never more than 4 times, this is clearly a Phone Keypad/Multi-Tap Cipher, aka what you get when you use an older phone to text someone.
After decoding that message we get: bitly.opoxmas.
So we go to http://bitly.com/opoxmas and we're redirected to the page with the flag: